
Red Team Services
We’ve transformed red teaming by extending the limited, short-lived scope of conventional consultancy exercises, making threat detection and deflection both constant and far more effective.
Digital
Lifelike attack simulations that will secure genuine value and unparalleled new levels of security.
Physical
Realistic physical attacks giving you complete confidence in what should be your first line of defense.
Social
Attacks to expose human-related risks, helping you instill a positive and thriving security culture.

We don’t play by the rules
Although we’ll always abide by the clearly defined circumstances under which we launch our simulated attacks on your organization, there are rules we don’t play by.
While your systems will never be at any genuine risk, we will act just like a real bad actor. It’s the only way to disclose breach points in your organization’s constantly-evolving attack surface.

Red teaming accredited by CREST
Our red team services are delivered by a vetted, fully-employed and multitalented global team of ethical hackers.
Their collective expertise was instrumental in our full accreditation by the Council for Registered Ethical Security Testers (CREST) for Simulated Targeted Attack and Response. And we’re one of only a few cyber vendors in the world to achieve this for our red teaming services.
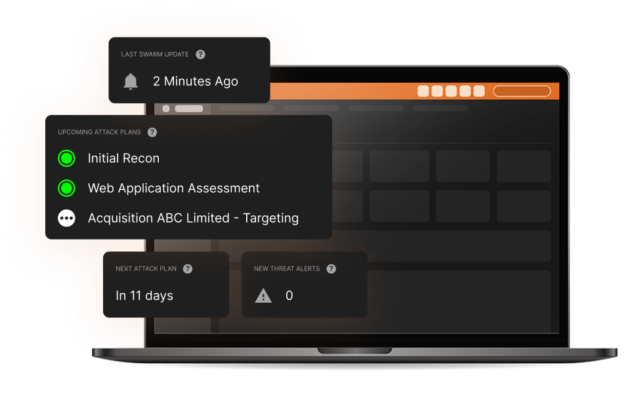
Collective
intelligence
The collective hive mind of our Swarm of ethical hackers is incorporated on our attack surface management portal – a library of discovered vulnerabilities and live attack surface mapping which can, in real time, direct them to any areas of a business and enable them to stay on top of their constantly evolving attack perimeter.
For our clients, this proprietary offensive exploration engine delivers significant value via long-term insights and instant access to each of our cyber attack simulations.
Names you know. If we could tell you.
For us, client confidentiality is key. So, while we can’t reveal names, you can trust us when we say that some of the world’s leading organizations trust their cybersecurity to us.
“WE ARE REALLY HAPPY WITH COVERTSWARM AS OUR EXTERNAL RED TEAM.”
COO and Co-founder, IT services and consulting company.
Attackers don’t rest. neither do we.
Cyber attacks are a constant threat. This is why testing on a six or twelve month cycle is no longer enough. Our subscription-based approach means the value delivered by our constant red team assault on your organization will be non-stop.
Via the CovertSwarm Portal you’ll have complete control over which areas of your business are attacked. We’ll respect boundaries and never place your systems in any genuine danger. But we can’t promise we’ll always play by the traditional rules of testing.
CovertSwarm subscription includes
- Constant cyber attack insights delivery
- Access to the CovertSwarm Portal
- Monthly ethical hacker time
- Dedicated account management via a senior CovertSwarm ethical hacker

The value of confidence
Starting from less than the cost of a single internal security hire, we have cybersecurity solutions for companies of all sizes, from SMEs up to enterprises, including discounted rates for public institutions, charities and B Corps.
Insights from the SWArm mind
Radical thinking and constant research inform all we do. Think ahead with shared intelligence from the CovertSwarm experts.

AI apps are smart. Until they do something really dumb.
AI apps seem brilliant—until they expose secrets or spill user data without a clue. Behind the curtain? Chaos. Hunters, take aim.

CovertSwarm Ranks #23 on Clutch 100 Fastest-Growing Companies in 2025
Clutch has recognized us for achieving one of the highest revenue growth rates from 2023 to 2024.

CovertSwarm Achieves Prestigious CBEST Accreditation, Cementing Industry Leadership in Financial Cybersecurity
CovertSwarm becomes one of the few cybersecurity firms accredited under the Bank of England’s rigorous CBEST framework.
Our services
Successful organizations are constant targets for malicious actors. Those who take security seriously don’t test their defenses once a year, they subscribe to CovertSwarm to attack continuously through our services.
- Breach and Attack Services
- Physical Cyber Attack Services
- Attack Surface Management Portal
- Social Engineering Services
- Penetration Testing Services
- Ethical Hacking Services
- Vulnerability Scanning
- Web Application Testing
- Ransomware Attack Simulation
- Phishing Attack Simulation
- Insider Threat Detection
- Password Strength Testing
- IT Infrastructure Testing