An In-Depth Guide to Remote Desktop Protocol (RDP)
The continually changing nature of today's workplace has made remote access technology essential.
The continually changing nature of today's workplace has made remote access technology essential.

The continually changing nature of today’s workplace has made remote access technology essential. The Remote Desktop Protocol (RDP) is an important technology that facilitates smooth remote access.
Microsoft created the Remote Desktop Protocol (RDP), which enables users to connect to another computer via a network and view a graphical user interface. Through Remote Desktop Protocol (RDP), a user may access a remote computer’s desktop and apps just like they would if they were in front of it. Since its first introduction in 1998 as part of Windows NT 4.0 Terminal Server Edition, this technology has transformed into a widely used tool for remote access and management.
RDP’s primary objective in our day-to-day is to make remote work, technical help, and administrative tasks easier. Helpdesk teams use it to diagnose problems without requiring physical access to the equipment. IT professionals use it to remotely manage servers and workstations, while businesses use it to allow employees to work from their homes.
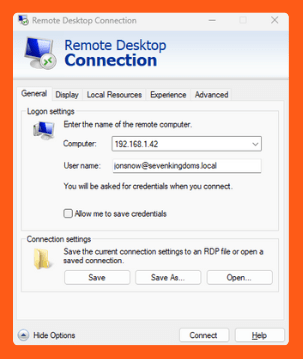
RDP works through a client-server architecture. The RDP server is installed on the computer that must be accessed remotely, and the RDP client is installed on the device that connects to it. The user’s input, which consists of keyboard and mouse clicks, is captured by the client software and sent to the server, which processes it and returns the graphical result to the client. This is usually done using port 3389, the default port for RDP traffic assigned by Microsoft.
Due to it being a common port, using it as the RDP port can pose security risks. Cyber attackers often scan for open ports to find potential targets to perform brute-force attacks and other malicious activities.
RDP has a variety of features that make it an effective tool for remote access and management. Some of the important aspects are:
RDP has several practical applications across multiple sectors and use cases. Some common applications include:
While RDP provides numerous advantages, it also introduces security vulnerabilities that must be addressed to provide safe and secure remote access. Some typical security vulnerabilities related to RDP include:
To reduce these risks, it is important to implement these best practices for securing RDP.
Although RDP is a widely used option for remote access, there are several other alternatives as well, each with unique features and advantages.

Everyone has a plan until they get punched in the face: reflections on the NCSC 2025 annual review
The NCSC Annual Review 2025 delivers a reality check. Highly significant cyber incidents have increased by 50 percent year over year. It’s time to act.

Part 3: CBEST Series – The Future of Threat-Led Penetration Testing
Regulated testing like CBEST is pivotal, but as threats shift, organizations must adopt more strategic, agile threat-led penetration testing. Discover what’s next.

Prime Day Scams – How Attackers Exploit Trust and Urgency
Every Prime Day, fake delivery texts flood inboxes, exploiting shoppers’ urgency and trust. We explain how these scams work and what both consumers and security teams…