Mitigating Credential Stuffing Attacks with IP Rotation: Strategies and Considerations
This article covers effective strategies to fight credential-stuffing attacks using IP rotation. By Ibai Castells
This article covers effective strategies to fight credential-stuffing attacks using IP rotation. By Ibai Castells
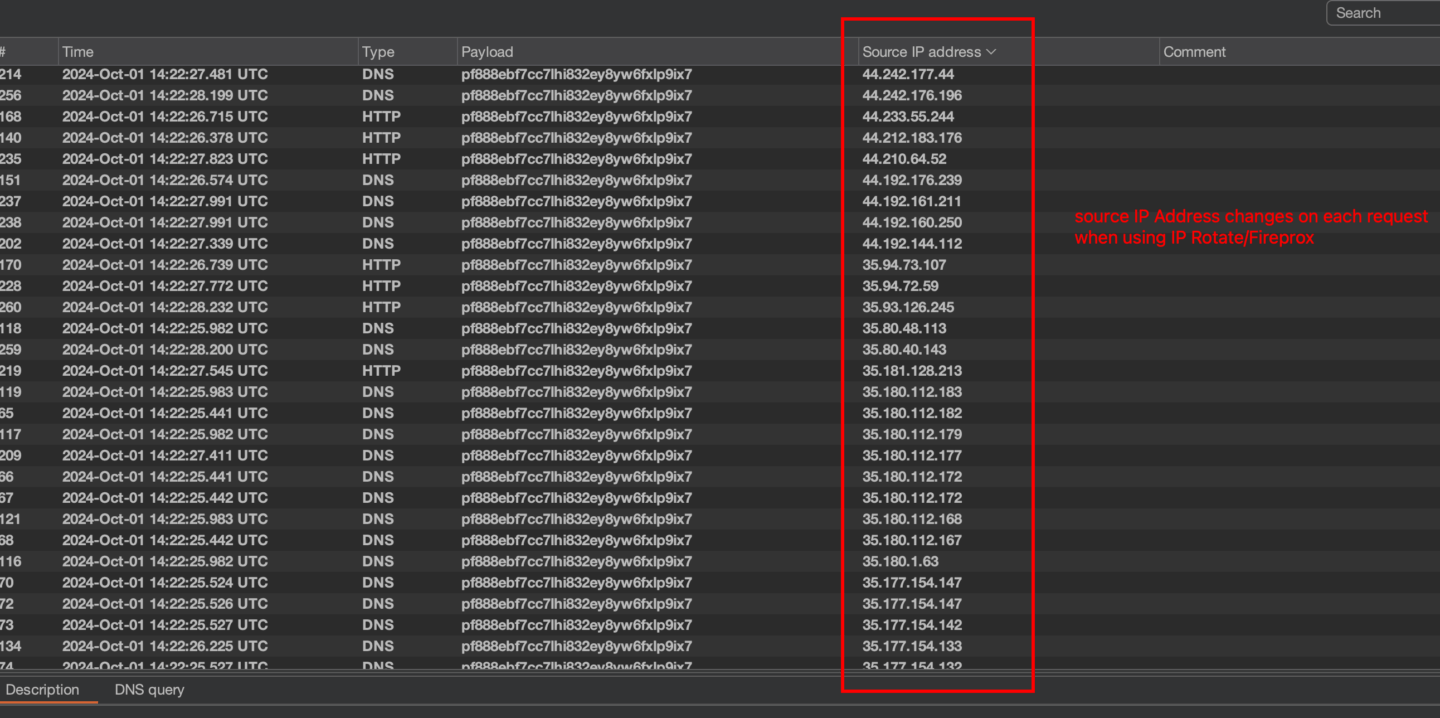
Credential stuffing attacks are still a major threat to organizations worldwide. Attackers use automated tools to “stuff” usernames and passwords on different endpoints, taking advantage of the fact that many people reuse credentials across multiple platforms. These attacks become significantly harder to detect when paired with IP rotation. This allows attackers to bypass standard rate-limiting and IP-based security measures and to obfuscate the geographical origin of the attack.
This article will cover effective strategies to fight credential-stuffing attacks using IP rotation. We will discuss user-agent-based detections, AWS API Gateway IP ranges, geofencing, multi-factor authentication (MFA), CAPTCHA, and advanced fingerprinting techniques. We will also cover the pros and cons of building in-house solutions versus using third-party tools for browser fingerprinting, as this solution has its intricacies due to data protection laws and modern browser technologies.
A simple way to spot malicious traffic is by checking the User-Agent (UA) strings in HTTP requests. Attackers often use automated tools with static or limited UA strings, which can be flagged as suspicious.
Action: Monitor and block requests with unusual or known bad UA strings. Additionally, keeping track of unusual User Agent strings across requests from different origins is one way to group requests from the same threat actor. This touches on the idea of browser fingerprinting, which will be discussed in more detail later in this post.
Attackers often use AWS API Gateway for IP rotation because tools like Fireprox and Burp Suite’s IP Rotate plugin make spinning up the required infrastructure easy and fast.
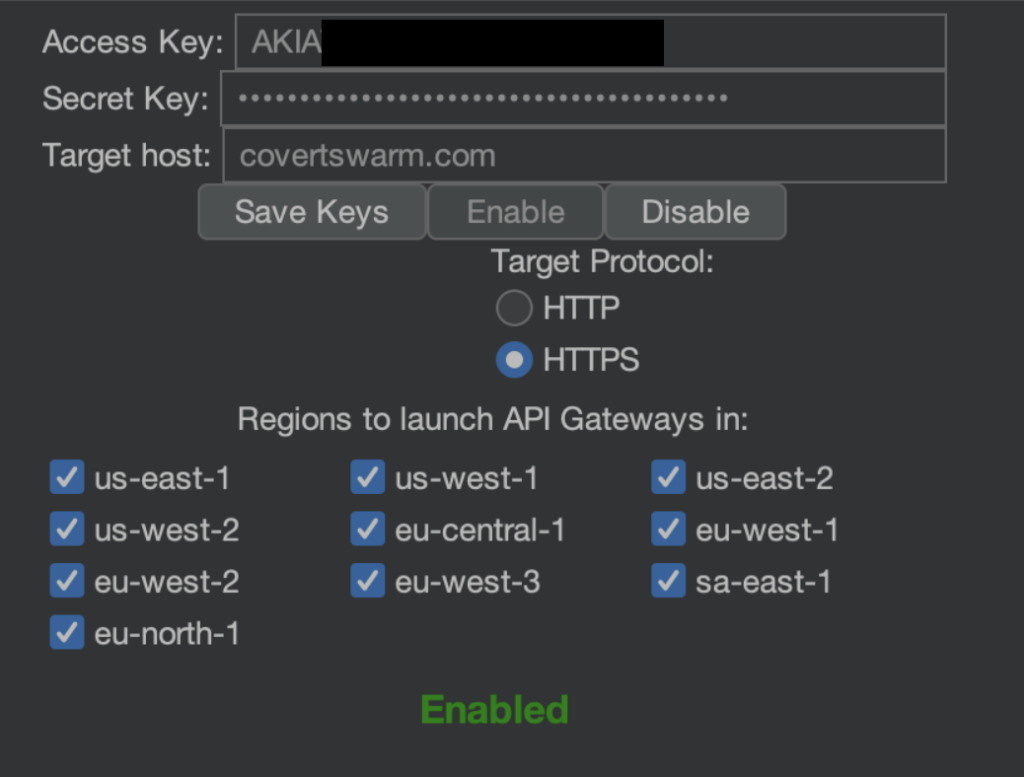
Action: Cross-check incoming IP addresses with AWS API Gateway’s IP ranges. If you do not use AWS API Gateway, consider blocking or applying stricter rules to these IPs.
Geofencing restricts access to your services based on geographic location.
Considerations:
Action: Use geofencing as one layer of your security approach, but don’t rely on it alone.
MFA adds an extra layer of security by requiring users to provide multiple forms of verification before they can access their accounts.
Action: Enforce MFA, especially for sensitive accounts or admin access.
CAPTCHAs are used to stop automated logins by requiring human verification.
Action: Use adaptive CAPTCHAs to reduce user friction while stopping automated attacks.
When attackers use IP rotation, traditional IP-based tracking becomes less effective. Fingerprinting tracks users based on the unique characteristics of their device or browser. Although this solution provides more flexibility and visibility of clients accessing your application, it comes with some complexity due to data regulations and modern browser privacy-focused features, which we all love but can be a double-edged sword when defending your assets.
How Fingerprinting Works
Action: Integrate fingerprinting into your security systems for better detection and response.
Risks and Considerations:
When It Makes Sense:
Benefits:
Options:
Considerations:
Credential stuffing attacks combined with IP rotation are complex threats, but they can be tackled with a multi-layered approach. Organizations can significantly improve their security by using user-agent analysis, IP range filtering, geofencing, MFA, CAPTCHA, and advanced fingerprinting.
Whether you choose to build your solution or use third-party tools depends on your needs and resources. A hybrid approach can offer flexibility and help you adapt as your needs change.
Success in combating these types of attacks requires careful planning, expertise, and constant monitoring. Staying proactive will help you protect your organization and users from these evolving attacks. Most importantly, as all of us involved in this industry know – cybersecurity is constantly evolving, and we must evolve with it. Creativity is one of the most powerful tools we have as humans, and applying it in these situations to create new solutions is a great way to defend our cyber estate.

SOC Testing: Turning Your Security Operations Centre into a Continuous Learning Engine
SOC testing isn’t just about finding vulnerabilities. It’s about building collaboration, sharpening human judgment, and turning your SOC into a continuous learning engine.

Why I founded CovertSwarm after annual pen tests failed me
Almost every business I worked for got breached. Our teams did the same thing each time: an occasional pen test, a thick report full of findings,…

When a former UK Government cyber operations chief says AI is “limitless” in Offensive Security, we should pay attention
Jim Clover says AI has made offensive cyber “limitless.” Attackers are using it now. The horse has already bolted. And if your red team isn’t keeping…