
Physical Cyber Attack Services
We dropped that infected USB drive, where we knew your staff would find it. We delivered the office lunch, and we’re now in your server room. That person next to your team in the coffee shop was us too, and we’ve now got your login details, along with the latest office news.
The benefits of in-person attack
The most effective methods of infiltration are often the crudest. So why should we remotely hack your systems when we could just steal a laptop from you? (And we don’t care if it’s encrypted, as we’ll break past that too.)
Our proven expertise in conducting realistic physical security attacks will give you complete confidence in what should be your first line of defense.
- Assess site security
- Expose physical vulnerabilities
- Explore untested environments
- Discover security blind spots
- Test and upskill your security culture

First, invite your worst nightmare to break in.
Engage the world’s best ethical hackers to launch a CovertSwarm physical attack on your organization, and you’ll have the most realistic assessment of the flaws in your security. Before any genuine bad actors exploit them.
You’ll also have the best possible advice on how to fix the problems we find. And our diverse Swarm of highly-skilled attackers will find problems.

Deeper Insights. Faster results.
Think hacking is only about shadowy figures meticulously crunching numbers to gain access to your systems? Think again. Physical cyber attacks, along with social engineering, are often the primary methods of infiltration.
The consequences of physical attacks on digital assets are severe. But with our joined-up, whole-brand attack approach, which sees us assault your organization from every angle, you’ll have deeper insights, faster results and longer-term protection. All via a simple subscription.
There’s no patch For complacency
Prevention is better than cure. And educating your people in security best practice is one of the best ways to prevent physical cyber attacks.
With CovertSwarm you won’t get a shiny-suited consultant with a slide deck they’ve shown to countless other clients. Real-world threats are best countered by people who actually carry them out for a job. Have us attack, and then reveal our tricks to your people to inspire, upskill and supercharge your security culture.
Constant cyber attack subscription
Our Constant Cyber Attack Subscription delivers relentless, full-spectrum assaults across your digital, physical, and social surfaces.
Forget rigid scopes and waiting weeks for a report. We give you a relentless adversary, attacking, probing, and exposing weaknesses before real attackers do. And if we can’t break in, you’ll know your security investments are working.
Schedule a call with our team to discuss how we can help outpace cyber threats.

STOP TESTING. START ATTACKING.
Just as your security defenses must evolve to keep pace with organizational change, so must your approach to cyber attack.
With most security breaches occurring many days prior to detection, effective simulated attacks must be constant. It’s the only way to counteract an APT and avoid zero-day exploits.

NO PATCH FOR HUMAN ERROR
It’s not just your systems and applications which are susceptible to threat. Your people are too. Staff members are one of the most common breach points for successful cyber attacks.
That’s why, thinking beyond the digital, we’ll seek to exploit previous unexplored weaknesses in your physical and social environments too.
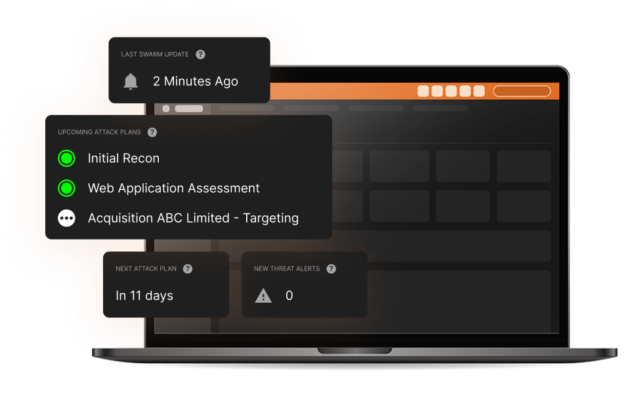
Collective
intelligence
The collective hive mind of our Swarm of ethical hackers is incorporated into our unique CovertSwarm Portal which can, in real time, direct our Swarm to any suspected weak areas of your business. It’s what enables us to put the ‘constant’ into ‘constant cyber attack’.
For you, a subscription will deliver significant value via long-term insights and instant access to our groundbreaking attack surface management portal, backed by our team of ethical hackers who are all fully employed by us.
REAL ATTACKERS DON’T REST. neither do we.
Cyber attacks are a constant threat. This is why testing on a six or twelve month cycle is no longer enough. Our subscription-based approach means the value delivered by our constant red team assault on your organization will be non-stop.
Via our CovertSwarm Portal you’ll have complete control over which areas of your business are attacked. We’ll respect boundaries and never place your systems in any genuine danger. But, just like a real attacker, we can’t promise we’ll always play by the traditional rules of testing.
CovertSwarm subscription includes:
- Constant cyber attack insights delivery
- Access to the CovertSwarm Portal
- Monthly ethical hacker time
- Dedicated account management via a senior CovertSwarm ethical hacker

The value of confidence
Starting from less than the cost of a single internal security hire, we have cybersecurity solutions for companies of all sizes, from SMEs up to enterprises, including discounted rates for public institutions, charities and B Corps.
Insights from the SWArm mind
Radical thinking and constant research inform all we do. Think ahead with shared intelligence from the CovertSwarm experts.

AI apps are smart. Until they do something really dumb.
AI apps seem brilliant—until they expose secrets or spill user data without a clue. Behind the curtain? Chaos. Hackers, take aim.

CovertSwarm Ranks #23 on Clutch 100 Fastest-Growing Companies in 2025
Clutch has recognized us for achieving one of the highest revenue growth rates from 2023 to 2024.

CovertSwarm Achieves Prestigious CBEST Accreditation
CovertSwarm becomes one of the few cybersecurity firms accredited under the Bank of England’s rigorous CBEST framework.
Our services
Successful organizations are constant targets for malicious actors. Those who take security seriously don’t test their defenses once a year, they subscribe to CovertSwarm to attack continuously through our services.
- Breach and Attack Simulation Services
- Attack Surface Management Portal
- Social Engineering Testing Services
- Red Team Services
- Penetration Testing Services
- Ethical Hacking Services
- Vulnerability Scanning
- Web Application Testing
- Ransomware Attack Simulation
- Phishing Attack Simulation
- Insider Threat Detection
- Password Strength Testing
- IT Infrastructure Testing



