



You deserve to be hacked
Telecoms is among the most-targeted sectors globally for cybercriminals. Those who take security seriously don’t test their defenses once a year.
They subscribe to CovertSwarm.
Evolving threats in a connected world
Playing a crucial role in global communication, the telecoms industry faces distinct cybersecurity challenges that affect both operations and clients, including (but certainly not limited to):
- Data breach
- Service disruption
- Financial losses
- Reputational damage
- Regulatory and legal consequences
The threat of cyber attack is constant. So are we.
You deserve to know when breach points appear in your organization’s constantly-evolving attack surface. The only way to achieve this is with a bad actor’s view. Which is where we come in.
How do we do it?
red team service cyber attacks
For a simple monthly subscription, our red team services will relentlessly launch realistic cyber attacks across the full scope of your brand, using digital, physical and social methods.
Digital
Lifelike attack simulations that will secure genuine value and unparalleled new levels of security.
Physical
Realistic physical attacks giving you complete confidence in what should be your first line of defense.
Social
Attacks to expose human-related risks, helping you instill a positive and thriving security culture.

We don’t play by the rules
Although we’ll always abide by the clearly defined circumstances under which we launch our simulated attacks on your organization, there are rules we don’t play by.
While your systems will never be at any genuine risk, we will act just like a real bad actor. It’s the only way to disclose breach points in your organization’s constantly-evolving attack surface.

Red teaming accredited by CREST
Our red team services are delivered by a vetted, fully-employed and multitalented global team of ethical hackers.
Their collective expertise was instrumental in our full accreditation by the Council for Registered Ethical Security Testers (CREST) for Simulated Targeted Attack and Response. And we’re one of only a few cyber vendors in the world to achieve this for our red teaming services.
Expertise. Endorsed.








Collective
intelligence
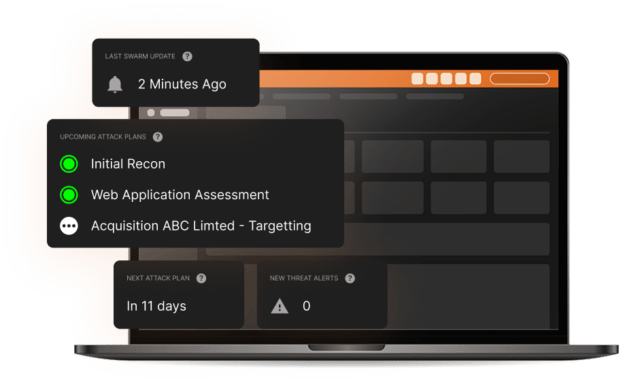
The collective hive mind of our Swarm of ethical hackers is incorporated into our unique Offensive Operations Center platform which can, in real time, direct our Swarm to any suspected weak areas of your business. It’s what enables us to put the ‘constant’ into ‘Constant Cyber Attack’.
For you, a subscription will deliver significant value via long-term insights and instant access to our groundbreaking platform, backed by our team of ethical hackers who are all fully employed by us.
Names you know. If we could tell you.
For us, client confidentiality is key. So, while we can’t reveal names, know that the world’s leading organizations trust their offensive cybersecurity needs to us.
“We are really happy with CovertSwarm as our external RED team.”
COO & Co-founder, IT services and consulting company